- Microsoft Ftp 7.5 Exploit
- Microsoft Ftpd Exploit Settings
- Microsoft Ftpd 5.0 Exploit
- Microsoft Ftpd Exploit Failed
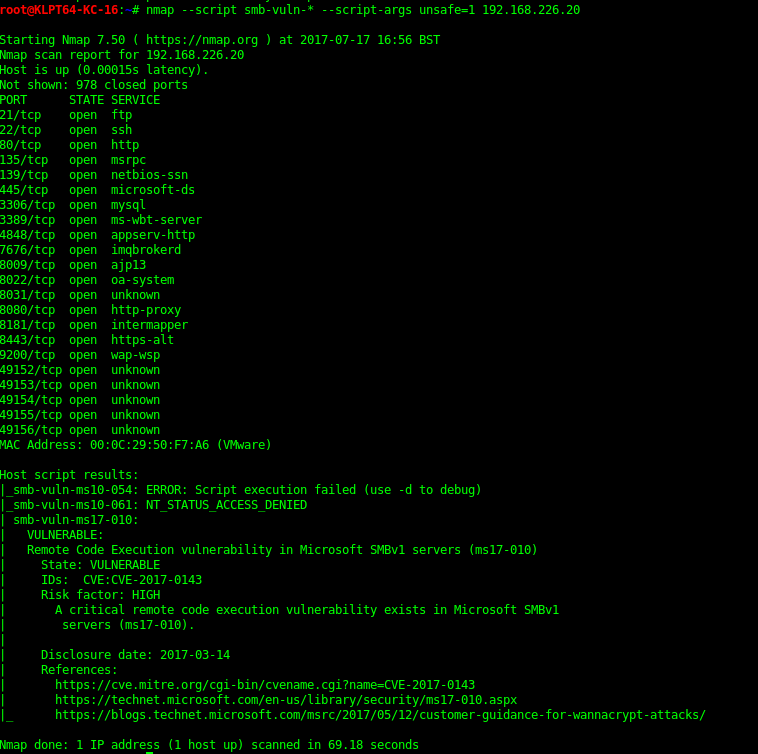
- Microsoft Ftpd Exploit Rapid7
- Microsoft Ftpd Exploit App
Tally is enumeration galore, full of red herrings, distractions, and rabbit holes. I spent hours digging through files and directories on this one. Tally will test your patience but it felt like a very realistic box so I enjoyed it. An interesting exploit at the end as well. Let’s get started!
Msf auxiliary (ftpversion) exploit From given image you can read the highlighted text which is showing vsftpd 3.0.2 is the installed version of FTP on target’s system. Microsoft Ftpd Exploit Free Public Access Press question mark to learn the rest of the keyboard shortcuts Log in sign up User account menu 9 Finding VulnerabilitiesExploits. An example - the nmap scan for a machine on a pentesting challenge site has come back with this: 21tcp open ftp Microsoft ftpd.
Enumeration
As always an nmap scan to get us going.
So we have a few interesting services to take a look at, including a SharePoint site. Lucky for us seclists has a wordlist specifically for SharePoint. Let’s fire up gobuster and see what we get.
Great… so we can see we have a ton of stuff to look through. None of the layouts or vti_bin stuff looks particularly interesting. /shared documents/forms/allitems.aspx and /sitedirectory/_layouts/viewlsts.aspx do look like good ones to check. Let’s start there.
We can see that there is one document and also a site page listed from the directory. If you click the links the server likes to rewrite the URL and insert in _layouts/15/start.aspx#/. If you remove it then you’ll get to your correct destination.
If we check out the Documents page, we are presented with the following:
Excellent, some ftp details. After downloading, we open and are presented with the following information:
No username though. Let’s check the site pages and see if there’s anything there.
We now have the username and password to take a look at FTP. Let’s log in.
We’re presented with a few directories, after digging for a while we find a few interesting things. First in Sarah’s folder inside the User directory we find a note.
Not of much use, but still good information to have. In Tim’s folder we find something much more interesting.
Let’s grab that KeePass database and see if we can crack the password on it.
Now that we have our hash we can run against hashcat. Remove tim: from the hash before trying to crack. I run hashcat on my Windows host.
Tim’s password is simplementeyo. Let’s open up the database with Keepass. We find three entries. The only one of real interest is some share credentials.
Let’s check these credentials with smbclient.
Microsoft Ftp 7.5 Exploit
Ah yes more folders to dig through. There is quite a bit of stuff here along with a few red herrings.
First we find some SQL connection information inside the zz_Archived folder.
This information gets us nothing and is just a distraction. We also find an interesting zip file.
The zip file is password protected. Let’s crack it with fcrackzip.
We can see the INSERT statement is adding the admin user with a password of Finance2. However we know from Sarah’s note earlier that the Orchard CMS is gone and it certainly doesn’t seem to be running on any of the ports. Again another red herring.
Back to enumerating!
tester.exe looks interesting and seems to be custom. Let’s download it and see what we can find out about it with strings
The output of strings is very long, but about midway we find what we need.
Finally! The sa password!
Let’s try to enable xp_cmdshell so we can get command execution on the box. Note: you will probably have to renable this a few times, it seems to disable automatically after a certain period of time.
We can test command execution now.
If we try to execute certain commands we get the following error:
To work around this we can prepend our commands by changing directories to C:.
We have a Server 2016 box which most likely means that if we try to upload a payload generated by msfvenom it’s probably going to get caught by Windows Defender. There’s actually a note on Sarah’s desktop confirming she enabled Defender and also patched the system.
To get around this we can use Veil. I used the python/shellcode_inject/aes_encrypt.py payload for a windows/meterpreter/reverse_tcp connection.
After generating the exe we can upload via FTP to the Intranet folder. We know we have write permissions there from the instructions on the SharePoint Finance page from earlier.
Now we can start our handler in Metasploit.
Execute our payload via SQL.
Woohoo! Finally we have a shell!
Privilege Escalation
We find some more red herrings on Sarah’s desktop.
This bat file gets ran at startup but it’s running the processes as Sarah so that doesn’t do it much good. The version of Firefox also seems to be vulnerable, however it’s not much use to us. There’s also some SharePoint Service warm up script and xml on the desktop, but again this is useless.
What is interesting is Sarah’s account is running as the SQL service account. So maybe we can elevate with this knowledge since service accounts usually have special privileges.
I won’t go into the details on how this exploit works, the article above explains it far better than I ever could.
Let’s check our privileges with meterpreter.
Excellent, it looks like we have the privileges we need to perform the attack. Let’s upload rottenpotato.exe to the Intranet folder via FTP.
Microsoft Ftpd Exploit Settings
Back on our meterpreter session we load the incognito extension.
We can see we currently have no Impersonation Tokens. Let’s run the Rotten Potato exploit.
We need to quickly impersonate the token or it will disappear.
Success! We have our SYSTEM shell and can grab the root.txt file!
If an attacker can accurately identify the target FTP service and the operating platform and architecture of the target server, it is relatively straightforward to identify and launch process-manipulation attacks to gain access to the server.
Most serious remote buffer overflows in FTP services are post-authentication issues; they require authenticated access to the FTP service and its underlying commands. Increasingly, write access is also required to create complex directory structures server-side that allow exploitation.
8.6.1 Solaris and BSD FTP Globbing Issues

The following glob( ) bug is present in default Solaris installations up to Solaris 8. By issuing a series of CWD~username requests, an attacker can effectively enumerate valid user accounts without even logging into the FTP server. This issue is described in detail at http://www.iss.net/security_center/static/6332.php and demonstrated in Example 8-6.
Example 8-6. Exploiting Solaris FTP glob( ) issues remotely
In the example, blah and test users don't exist, but chris does. A similar postauthentication glob( ) bug can be exploited, which result in a heap overflow. Example 8-7 details how local users can easily abuse this vulnerability, resulting in a core dump containing encrypted user passwords from the /etc/shadow file. These two issues are referenced within the MITRE CVE list as CVE-2001-0421.
Example 8-7. Exploiting Solaris FTP glob( ) issues locally
No public preauthentication exploits have been released to compromise Solaris hosts by abusing glob( ) issues. Theoretically, the service can be exploited under Solaris if write access to the filesystem is permitted through FTP (see CVE-2001-0249), although this may be difficult to exploit under Solaris.
The glob( ) function called by FTP is also vulnerable to attack under BSD-derived systems (NetBSD, OpenBSD, and FreeBSD) due to the way heap memory is managed. An exploit script for this issue is available at http://www.phreak.org/archives/exploits/unix/ftpd-exploits/turkey2.c.
8.6.2 WU-FTPD Vulnerabilities
WU-FTPD is a popular and easy-to-manage FTP service that many system administrators run across multiple Unix-like platforms (primarily Linux). Here, I present a breakdown of recent serious remotely exploitable (omitting denial-of-service or locally exploitable issues) vulnerabilities in various versions of WU-FTP, with details of working exploit scripts. For the latest details of bugs in this software, Be sure to heck the MITRE CVE and ISS X-Force databases at http://cve.mitre.org and http://xforce.iss.net, respectively.
By creating a complex directory structure and issuing a DELE command, a stack overflow occurs. An exploit is available for Linux targets at http://examples.oreilly.com/networksa/tools/w00f.c, and further information is available at http://xforce.iss.net/xforce/xfdb/1728.
Microsoft Ftpd 5.0 Exploit
This is exploitable by creating a complex directory structure and issuing a series of CWD commands, resulting in a stack overflow. An exploit is available for Linux targets at http://examples.oreilly.com/networksa/tools/ifafoffuffoffaf.c, and further information is available at http://xforce.iss.net/xforce/xfdb/3158.
This is exploitable by issuing a crafted SITE EXEC command on the FTP server, resulting in the exploitation of a format string bug. Various scripts exist to exploit this under FreeBSD and various Linux distributions, of which a favorite of mine is http://examples.oreilly.com/networksa/tools/wuftp-god.c. Background information is available at http://xforce.iss.net/xforce/xfdb/4773.
By issuing a series of RNFR and CWD ~{ commands to the FTP service, a heap overflow occurs through the glob( ) function. TESO released the excellent 7350wurm exploit script to compromise various Linux distributions, available at http://examples.oreilly.com/networksa/tools/7350wurm.c. Further information is available at http://xforce.iss.net/xforce/xfdb/7611.
The realpath( ) function within WU-FTP contains an off-by-one bug, which you can exploit by issuing a number of FTP commands (including STOR, RETR, MKD, and RMD). An exploit that compromises various Linux distributions is available at http://examples.oreilly.com/networksa/tools/0x82-wu262.c. You should check MITRE CVE at http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-0466 for information because the ISS X-Force web site doesn't list any details for this issue at the time of writing.
8.6.2.1 Exploiting WU-FTPD 2.6.1 on Linux with 7350wurm
The 7350wurm exploit can root most Linux WU-FTPD services through its in-built list of targets. The usage of the tool is shown in Example 8-8.
Example 8-8. 7350wurm usage
One excellent trick that 7350wurm has up its sleeve is that it can exploit a large number of WU-FTPD servers found running out-of-the-box on Linux hosts, reflected in Example 8-9.
Example 8-9. The 7350wurm target list
7350wurm can be run easily with the -a flag, grabbing the banner of the target FTP server and selecting the correct offsets from its target list, shown in Example 8-10.
Example 8-10. wurm running in automatic mode
8.6.3 ProFTPD Vulnerabilities
Microsoft Ftpd Exploit Failed
ProFTPD is similar to WU-FTPD in that it can be run from multiple operating platforms. I often see ProFTPD running on FreeBSD and Slackware Linux in the wild. Table 8-3 lists recent serious remotely exploitable issues in ProFTPD as listed in the MITRE CVE at the time of writing.
CVE name | Date | Notes |
|---|---|---|
CAN-1999-0911 | 27/08/1999 | ProFTPD 1.2.0pre5 and prior MKD and CWD nested directory stack overflow. |
CAN-2000-0574 | 06/07/2000 | ProFTPD prior to 1.2.0rc2 contains multiple format string vulnerabilities that can be exploited remotely. |
CAN-2003-0831 | 23/09/2003 | ProFTPD 1.2.7 to 1.2.9rc2 ASCII transfer mode newline character overflow. |
Public exploit code for two of the CVE candidate references listed in Table 8-3 can be found in the Packet Storm archives.
CAN-1999-0911, MKD and CWD stack overflow can be found at the following:
- http://packetstormsecurity.org/groups/teso/pro.tar.gz
- http://packetstormsecurity.org/advisories/b0f/proftpd.c
- http://packetstormsecurity.org/0007-exploits/proftpX.c
CAN-2003-0831, ASCII transfer mode newline character overflow can be found at http://packetstormsecurity.org/0310-exploits/proftpdr00t.c.
8.6.4 Microsoft IIS FTP Server
Microsoft Ftpd Exploit Rapid7
At the time of writing, the only serious vulnerabilities that threaten Microsoft IIS FTP services are denial-of-service issues, usually exploitable through an authenticated FTP session. Two remotely exploitable security issues in the IIS 4.0 and 5.0 FTP services are listed within MITRE CVE as CVE-2001-0335 and CVE-1999-0777; both are medium-risk issues relating to information leakage from the service.
Microsoft Ftpd Exploit App
A common oversight is for system administrators to set up Internet-based IIS FTP servers and leave anonymous guest access to the server enabled.I have seen such open servers used as public storage and distribution centers for pirated software and other material.
